Harper Alert: Due to extreme cold, Harper College campuses will be closed Friday, January 23. Learn more: http://bit.ly/36jRbZ8
You may not realize it, but you are a phishing target at school, at work, and at home. Ultimately, you are the most effective way to detect and stop phishing scams. When viewing e-mail messages, texts, or social media posts, look for the following indicators to prevent stolen passwords, personal data, or private information.
Beware sketchy messages. Phishy messages may include a formal salutation, overly-friendly tone, grammatical errors, urgent requests, or gimmicks.
Avoid opening links and attachments.Even if you know the sender, don't click on links that could direct you to a bad website. And do not open attachments unless you are expecting a file from someone.
Verify the source. Check the sender's e-mail address to make sure it's legitimate. If in doubt, just delete the message.
The Federal Trade Commission (FTC) has released recommendations for consumers to protect their personal data when using rental vehicles. Rental vehicles may contain infotainment systems that can connect with personal devices to stream music, allow hands-free calls and texts, or guide navigation. However, using connected vehicles can increase the risks of having personal data compromised. By taking precautions, users can protect themselves and their personal information.
Symantec and Norton branded antivirus products contain multiple vulnerabilities. Continue reading...
Be safe and secure when reading email or browsing online.
Use private networks for sensitive transactions. Avoid checking your bank account, making purchases or logging in to other websites that include sensitive information when using public Wi-Fi.
Go stealth when browsing. Your browser can store quite a bit of information about your online activities, including cookies, cached pages and history. To ensure the privacy of personal information online, limit access by going "incognito" and using the browser's private mode: Private browsing in IE, Private browsing in Firefox, Incognito mode in Chrome
Be more secure! Make sure a URL includes HTTPS before entering any personal information.
When in doubt, ignore. Don't click on pop-up windows or extraneous ads.
Keep your private information safe. Use a strong, unique password or passphrase for each account and avoid storing account information on a website. Consider using separate browsers for sensitive logins and general web browsing.
Keep your browser software up-to-date on your personal devices. Be sure to install antivirus updates and regularly check for and install browser plugin (e.g., Adobe Flash and Java) updates. Contact the Service Desk for updates on your Harper devices. Learn more about antivirus software.
Mobile phones, tablets, and laptops continue to provide us with the opportunity to work "on the go," but this added convenience could also mean more risk. These personal devices are making it easier to store and access information, but they are also easy to steal or misplace. Do you know what to do if your device is lost or stolen?
Secure your devices. Use a passphrase, password, or fingerprint to secure your device from casual intrusion.
Turn on location tracking. If your device has a "Find Me" feature (such as Apple's iCloud service to "Find My iPhone") make sure it is enabled. Or investigate third-party software to help you recover your devices.
Write it down! Record the manufacturer, model, and serial numbers of your mobile devices and store the info in a safe place.
Notify providers. Keep important phone numbers such as your cell phone provider or IT support department handy so you can quickly report the device as lost or stolen. In some cases the cell provider or your support desk may be able to deactivate and wipe the device for you remotely.
Encrypt and backup information. Determine if your device encrypts your data at rest. That way if it's stolen, you just lose the device and don't open yourself to identity theft. If your device doesn't use encryption by default, enable it or install encryption software. Don't forget to backup information on all of your mobile devices too. Learn more about encryption and how to tell if you have encryption working.
File a report. If your device is stolen, file a police report immediately.
BEC is defined as a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. Continue reading...
Each year, criminal actors target US persons and visa holders for Stolen Identity Refund Fraud (SIRF). Continue reading...
You and your information are everywhere. When you're online you leave a trail of "digital exhaust" in the form of cookies, GPS data, social network posts, and e-mail exchanges, among others. It is critical to learn how to protect yourself and guard your privacy. Your identity and even your bank account could be at risk!

Use long and complex passwords or passphrases. These are often the first line of defense in protecting an online account. The length and complexity of your passwords can provide an extra level of protection for your personal information.
Take care what you share.Periodically check the privacy settings for your social networking apps to ensure that they are set to share only what you want, with whom you intend. Be very careful about putting personal information online. What goes on the Internet usually stays on the Internet.
Go stealth when browsing. Your browser can store quite a bit of information about your online activities, including cookies, cached pages, and history. To ensure the privacy of personal information online, limit access by going "incognito" and using the browser's private mode.
Using Wi-Fi? If only public Wi-Fi is available, restrict your activity to simple searches (no banking!) or use a VPN (virtual private network). The latter provides an encrypted tunnel between you and the sites you visit.
Should you trust that app? Only use apps from reputable sources. Check out reviews from users or other trusted sources before downloading anything that is unfamiliar.
In early 2016, destructive ransomware variants such as Locky and Samas were observed infecting computers belonging to individuals and businesses, which included health care facilities and hospitals worldwide. Continue reading...
Planning a vacation? People are frequently more vulnerable when traveling because a break from their regular routine or encounters with unfamiliar situations often result in less cautious behavior. If this sounds like you, or someone you know, these five tips will help you protect yourself and guard your privacy.
All software products have a lifecycle. Apple will no longer be providing security updates for QuickTime for Windows. Continue reading...
With an increasing amount of sensitive data being stored on personal devices, the value and mobility of smartphones, tablets, and laptops make them appealing and easy targets. These simple tips will help you be prepared in case your laptop is stolen or your smartphone is misplaced.
Don't leave your device alone, even for a minute! If you're not using it, lock your device in a cabinet or drawer, use a security cable, or take it with you. It's not enough to simply ask the stranger next to you in a library or coffee shop to watch your laptop for a few minutes.
Differentiate your device. It's less likely that someone will steal your device and say they thought it belonged
to them if your device looks unique. Sometimes these markings make the laptop harder
to resell, so they're less likely to be stolen. Use a permanent marking, engraving,
or tamper-resistant commercial asset tracking tag.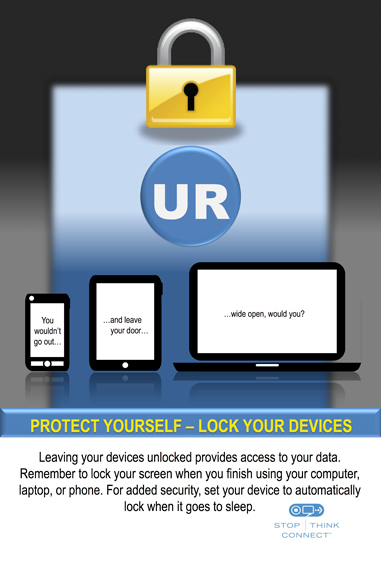
Delete sensitive information. Don't keep any restricted data on your laptop. We recommend searching your computer for restricted data and deleting it. Restricted data includes your Social Security number, credit card numbers, network IDs, passwords, and other personally identifiable information. You'd be surprised how easy it is to forget that this information is on your computer!
Back it up. Set a reminder to backup your data on a regular basis! Keep an external copy of important files stored on your laptop in a safe location in case it is lost or stolen. Your photos, papers, research, and other files are irreplaceable, and losing them may be worse than losing your device.
Encrypt information. Protect your personal data with the built-in disc encryption feature included with your computer's operating system (e.g., BitLocker or FileVault).
Record the serial number. Jot down the serial number of your device and store it in a safe place. This information can be useful for verifying your device if it's found.
Install software. Install and use tracking and recovery software included with most devices (e.g., the "Find iDevice" feature in iOS) or invest in commercial products like LoJack or Prey. Some software includes remote-wipe capabilities. This feature allows you to log on to an online account and delete all of the information on your laptop. There are both paid and free versions of this type of software, and each provides different levels of features. Search online to find the best combination of cost and functions to meet your needs.
At least 36 organizations worldwide are affected by an SAP vulnerability. Security researchers from Onapsis discovered indicators of exploitation against these organizations’ SAP business applications. Continue reading....